Nextcloud Server Service
Table of Contents
Defined in /modules/services/nextcloud-server.nix.
This NixOS module is a service that sets up a Nextcloud Server. It is based on the nixpkgs Nextcloud server and provides opinionated defaults.
Features
Declarative Apps Configuration - no need to configure those with the UI.
LDAP app: enables app and sets up integration with an existing LDAP server, in this case LLDAP. Note that the LDAP app cannot distinguish between normal users and admin users.
SSO app: enables app and sets up integration with an existing SSO server, in this case Authelia. The SSO app can distinguish between normal users and admin users.
Preview Generator app: enables app and sets up required cron job.
External Storage app: enables app and optionally configures one local mount. This enables having data living on separate hard drives.
Only Office app: enables app and sets up Only Office service.
Memories app: enables app and sets up all required dependencies and optional hardware acceleration with VAAPI.
Recognize app: enables app and sets up all required dependencies and optional hardware acceleration with VAAPI.
Any other app through the shb.nextcloud.extraApps option.
Access through subdomain using reverse proxy.
Forces Nginx as the reverse proxy. (This is hardcoded in the upstream nixpkgs module).
Sets good defaults for trusted proxies settings, chunk size, opcache php options.
Access through HTTPS using reverse proxy.
Forces PostgreSQL as the database.
Forces Redis as the cache and sets good defaults.
Backup of the
shb.nextcloud.dataDirthrough the backup block.Monitoring Dashboard for monitoring of reverse proxy, PHP-FPM, and database backups through the monitoring block.
Integration with the dashboard contract for displaying user facing application in a dashboard.
Tests system cron job is setup correctly.
Tests initial admin user and password are setup correctly.
Tests admin user can create and retrieve a file through WebDAV.
Enables easy setup of xdebug for PHP debugging if needed.
Easily add other apps declaratively through [extraApps][]
By default automatically disables maintenance mode on start.
By default automatically launches repair mode with expensive migrations on start.
Access to advanced options not exposed here thanks to how NixOS modules work.
Has a demo.
Usage
- Nextcloud through HTTP
- Nextcloud through HTTPS
- Choose Nextcloud Version
- Mount Point
- With LDAP Support
- With SSO Support
- Tweak PHPFpm Config
- Tweak PostgreSQL Settings
- Backup
- Application Dashboard
- Enable Preview Generator App
- Enable External Storage App
- Enable OnlyOffice App
- Enable Memories App
- Enable Recognize App
- Enable Monitoring
- Enable Tracing
- Appdata Location
Nextcloud through HTTP
Note
This section corresponds to the basic section of the Nextcloud
demo.
Configuring Nextcloud to be accessible through Nginx reverse proxy
at the address http://n.example.com,
with PostgreSQL and Redis configured,
is done like so:
shb.nextcloud = {
enable = true;
domain = "example.com";
subdomain = "n";
defaultPhoneRegion = "US";
adminPass.result = config.shb.sops.secret."nextcloud/adminpass".result;
};
shb.sops.secret."nextcloud/adminpass".request = config.shb.nextcloud.adminPass.request;
This assumes secrets are setup with SOPS as mentioned in the secrets setup section of the manual.
Secrets can be randomly generated with nix run nixpkgs#openssl -- rand -hex 64.
Note though that Nextcloud will not be very happy to be accessed through HTTP, it much prefers - rightfully - to be accessed through HTTPS. We will set that up in the next section.
You can now login as the admin user using the username admin
and the password defined in sops.secrets."nextcloud/adminpass".
Nextcloud through HTTPS
To setup HTTPS, we will get our certificates from Let’s Encrypt using the HTTP method. This is the easiest way to get started and does not require you to programmatically configure a DNS provider.
Under the hood, we use the Self Host Block SSL contract. It allows the end user to choose how to generate the certificates. If you want other options to generate the certificate, follow the SSL contract link.
Building upon the Basic Configuration above, we add:
shb.certs.certs.letsencrypt."example.com" = {
domain = "example.com";
group = "nginx";
reloadServices = [ "nginx.service" ];
adminEmail = "myemail@mydomain.com";
};
shb.certs.certs.letsencrypt."example.com".extraDomains = [ "n.example.com" ];
shb.nextcloud = {
ssl = config.shb.certs.certs.letsencrypt."example.com";
};
Choose Nextcloud Version
Self Host Blocks is conservative in the version of Nextcloud it’s using. To choose the version and upgrade at the time of your liking, just use the version option:
shb.nextcloud.version = 29;
Mount Point
If the dataDir exists in a mount point,
it is highly recommended to make the various Nextcloud services wait on the mount point before starting.
Doing that is just a matter of setting the mountPointServices option.
Assuming a mount point on /var, the configuration would look like so:
fileSystems."/var".device = "...";
shb.nextcloud.mountPointServices = [ "var.mount" ];
With LDAP Support
Note
This section corresponds to the ldap section of the Nextcloud
demo.
We will build upon the HTTP and HTTPS sections, so please read those first.
We will use the LLDAP block provided by Self Host Blocks. Assuming it has been set already, add the following configuration:
shb.nextcloud.apps.ldap = {
enable = true;
host = "127.0.0.1";
port = config.shb.lldap.ldapPort;
dcdomain = config.shb.lldap.dcdomain;
adminName = "admin";
adminPassword.result = config.shb.sops.secret."nextcloud/ldap/adminPassword".result
userGroup = "nextcloud_user";
};
shb.sops.secret."nextcloud/ldap/adminPassword" = {
request = config.shb.nextcloud.apps.ldap.adminPassword.request;
settings.key = "ldap/userPassword";
};
The LDAP admin password must be shared between shb.lldap and shb.nextcloud,
to do that with SOPS we use the key option so that both
sops.secrets."ldap/userPassword"
and sops.secrets."nextcloud/ldapUserPassword"
secrets have the same content.
The LDAP user group is created automatically.
Add your user to it by going to http://ldap.example.com,
create a user if needed and add it to the group.
When that’s done, go back to the Nextcloud server at
https://nextcloud.example.com and login with that user.
Note that we cannot create an admin user from the LDAP server, so you need to create a normal user like above, login with it once so it is known to Nextcloud, then logout, login with the admin Nextcloud user and promote that new user to admin level. This limitation does not exist with the SSO integration.
With SSO Support
Note
This section corresponds to the sso section of the Nextcloud
demo.
We will build upon the HTTP, HTTPS and LDAP sections, so please read those first.
We will use the SSO block provided by Self Host Blocks. Assuming it has been set already, add the following configuration:
shb.nextcloud.apps.sso = {
enable = true;
endpoint = "https://${config.shb.authelia.subdomain}.${config.shb.authelia.domain}";
clientID = "nextcloud";
fallbackDefaultAuth = false;
secret.result = config.shb.sops.secret."nextcloud/sso/secret".result;
secretForAuthelia.result = config.shb.sops.secret."nextcloud/sso/secretForAuthelia".result;
};
shb.sops.secret."nextcloud/sso/secret".request = config.shb.nextcloud.apps.sso.secret.request;
shb.sops.secret."nextcloud/sso/secretForAuthelia" = {
request = config.shb.nextcloud.apps.sso.secretForAuthelia.request;
settings.key = "nextcloud/sso/secret";
};
The SSO secret must be shared between shb.authelia and shb.nextcloud,
to do that with SOPS we use the key option so that both
sops.secrets."nextcloud/sso/secret"
and sops.secrets."nextcloud/sso/secretForAuthelia"
secrets have the same content.
The LDAP user group and admin group are created automatically.
Add your user to one or both by going to http://ldap.example.com,
create a user if needed and add it to the groups.
When that’s done, go back to the Nextcloud server at
https://nextcloud.example.com and login with that user.
Setting the fallbackDefaultAuth to false means the only way to login is through Authelia.
If this does not work for any reason, you can let users login through Nextcloud directly by setting this option to true.
Tweak PHPFpm Config
For instances with more users, or if you feel the pages are loading slowly,
you can tweak the php-fpm pool settings.
shb.nextcloud.phpFpmPoolSettings = {
"pm" = "static"; # Can be dynamic
"pm.max_children" = 150;
# "pm.start_servers" = 300;
# "pm.min_spare_servers" = 300;
# "pm.max_spare_servers" = 500;
# "pm.max_spawn_rate" = 50;
# "pm.max_requests" = 50;
# "pm.process_idle_timeout" = "20s";
};
I don’t have a good heuristic for what are good values here but what I found
is that you don’t want too high of a max_children value
to avoid I/O strain on the hard drives, especially if you use spinning drives.
To see the effect of your settings, go to the provided Grafana dashboard.
Tweak PostgreSQL Settings
These settings will impact all databases since the NixOS Postgres module configures only one Postgres instance.
To know what values to put here, use https://pgtune.leopard.in.ua/. Remember the server hosting PostgreSQL is shared at least with the Nextcloud service and probably others. So to avoid PostgreSQL hogging all the resources, reduce the values you give on that website for CPU, available memory, etc. For example, I put 12 GB of memory and 4 CPUs while I had more:
DB Version: 14OS Type: linuxDB Type: dwTotal Memory (RAM): 12 GBCPUs num: 4Data Storage: ssd
And got the following values:
shb.nextcloud.postgresSettings = {
max_connections = "400";
shared_buffers = "3GB";
effective_cache_size = "9GB";
maintenance_work_mem = "768MB";
checkpoint_completion_target = "0.9";
wal_buffers = "16MB";
default_statistics_target = "100";
random_page_cost = "1.1";
effective_io_concurrency = "200";
work_mem = "7864kB";
huge_pages = "off";
min_wal_size = "1GB";
max_wal_size = "4GB";
max_worker_processes = "4";
max_parallel_workers_per_gather = "2";
max_parallel_workers = "4";
max_parallel_maintenance_workers = "2";
};
To see the effect of your settings, go to the provided Grafana dashboard.
Backup
Backing up Nextcloud data files using the Restic block is done like so:
shb.restic.instances."nextcloud" = {
request = config.shb.nextcloud.backup;
settings = {
enable = true;
};
};
The name "nextcloud" in the instances can be anything.
The config.shb.nextcloud.backup option provides what directories to backup.
You can define any number of Restic instances to backup Nextcloud multiple times.
For backing up the Nextcloud database using the same Restic block, do like so:
shb.restic.instances."postgres" = {
request = config.shb.postgresql.databasebackup;
settings = {
enable = true;
};
};
Note that this will backup the whole PostgreSQL instance, not just the Nextcloud database. This limitation will be lifted in the future.
Application Dashboard
Integration with the dashboard contract is provided by the dashboard option.
For example using the Homepage service:
{
shb.homepage.servicesGroups.Documents.services.Nextcloud = {
sortOrder = 1;
dashboard.request = config.shb.nextcloud.dashboard.request;
};
}
Enable Preview Generator App
The following snippet installs and enables the Preview Generator application as well as creates the required cron job that generates previews every 10 minutes.
shb.nextcloud.apps.previewgenerator.enable = true;
Note that you still need to generate the previews for any pre-existing files with:
nextcloud-occ -vvv preview:generate-all
The default settings generates all possible sizes which is a waste since most are not used. SHB will change the generation settings to optimize disk space and CPU usage as outlined in this article. You can opt-out with:
shb.nextcloud.apps.previewgenerator.recommendedSettings = false;
Enable External Storage App
The following snippet installs and enables the External Storage application.
shb.nextcloud.apps.externalStorage.enable = true;
Adding external storage can then be done through the UI.
For the special case of mounting a local folder as an external storage,
Self Host Blocks provides options.
The following snippet will mount the /srv/nextcloud/$user local file
in each user’s /home Nextcloud directory.
shb.nextcloud.apps.externalStorage.userLocalMount = {
rootDirectory = "/srv/nextcloud/$user";
mountName = "home";
};
You can even make the external storage mount in the root / Nextcloud directory with:
shb.nextcloud.apps.externalStorage.userLocalMount = {
mountName = "/";
};
Recommended use of this app is to have the Nextcloud’s dataDir on a SSD
and the userLocalMount on a HDD.
Indeed, a SSD is much quicker than a spinning hard drive,
which is well suited for randomly accessing small files like thumbnails.
On the other side, a spinning hard drive can store more data
which is well suited for storing user data.
This Nextcloud module includes a patch that allows the external storage to actually create the local path. Normally, when login in for the first time, the user will be greeted with an error saying the external storage path does not exist. One must then create it manually. With this patch, Nextcloud creates the path.
Enable OnlyOffice App
The following snippet installs and enables the Only
Office application as well as sets up an Only Office
instance listening at onlyoffice.example.com that only listens on the local network.
shb.nextcloud.apps.onlyoffice = {
enable = true;
subdomain = "onlyoffice";
localNextworkIPRange = "192.168.1.1/24";
};
Also, you will need to explicitly allow the package corefonts:
nixpkgs.config.allowUnfreePredicate = pkg: builtins.elem (pkgs.lib.getName pkg) [
"corefonts"
];
Enable Memories App
The following snippet installs and enables the Memories application.
shb.nextcloud.apps.memories = {
enable = true;
vaapi = true; # If hardware acceleration is supported.
photosPath = "/Photos"; # This is the default.
};
All the following dependencies are installed correctly and fully declaratively, the config page is “all green”:
Exiftool with the correct version
Indexing path is set to
/Photosby default.Images, HEIC, videos preview generation.
Performance is all green with database triggers.
Recommended apps are
Reverse Geocoding must be triggered manually with
nextcloud-occ memories:places-setup.Video streaming is setup by installed ffmpeg headless.
Transcoder is setup natively (not with slow WASM) wit
go-vodbinary.Hardware Acceleration is optionally setup by setting
vaapitotrue.
It is not required but you can for the first indexing with nextcloud-occ memories:index.
Note that the app is not configurable through the UI since the config file is read-only.
Enable Recognize App
The following snippet installs and enables the Recognize application.
shb.nextcloud.apps.recognize = {
enable = true;
};
The required dependencies are installed: nodejs and nice.
Enable Monitoring
Enable the monitoring block. A Grafana dashboard for overall server performance will be created and the Nextcloud metrics will automatically appear there.
Enable Tracing
You can enable tracing with:
shb.nextcloud.debug = true;
Traces will be located at /var/log/xdebug.
See my blog post for how to look at the traces.
I want to make the traces available in Grafana directly
but that’s not the case yet.
Appdata Location
The appdata folder is a special folder located under the shb.nextcloud.dataDir directory.
It is named appdata_<instanceid> with the Nextcloud’s instance ID as a suffix.
You can find your current instance ID with nextcloud-occ config:system:get instanceid.
In there, you will find one subfolder for every installed app that needs to store files.
For performance reasons, it is recommended to store this folder on a fast drive that is optimized for randomized read and write access. The best would be either an SSD or an NVMe drive.
The best way to solve this is to use the External Storage app.
If you have an existing installation and put Nextcloud’s shb.nextcloud.dataDir folder on a HDD with spinning disks,
then the appdata folder is also located on spinning drives.
One way to solve this is to bind mount a folder from an SSD over the appdata folder.
SHB does not provide a declarative way to setup this
as the external storage app is the preferred way
but this command should be enough:
mount /dev/sdd /srv/sdd
mkdir -p /srv/sdd/appdata_nextcloud
mount --bind /srv/sdd/appdata_nextcloud /var/lib/nextcloud/data/appdata_ocxvky2f5ix7
Note that you can re-generate a new appdata folder
by issuing the command nextcloud-occ config:system:delete instanceid.
Demo
Head over to the Nextcloud demo for a demo that installs Nextcloud with or without LDAP integration on a VM with minimal manual steps.
Monitoring Dashboard
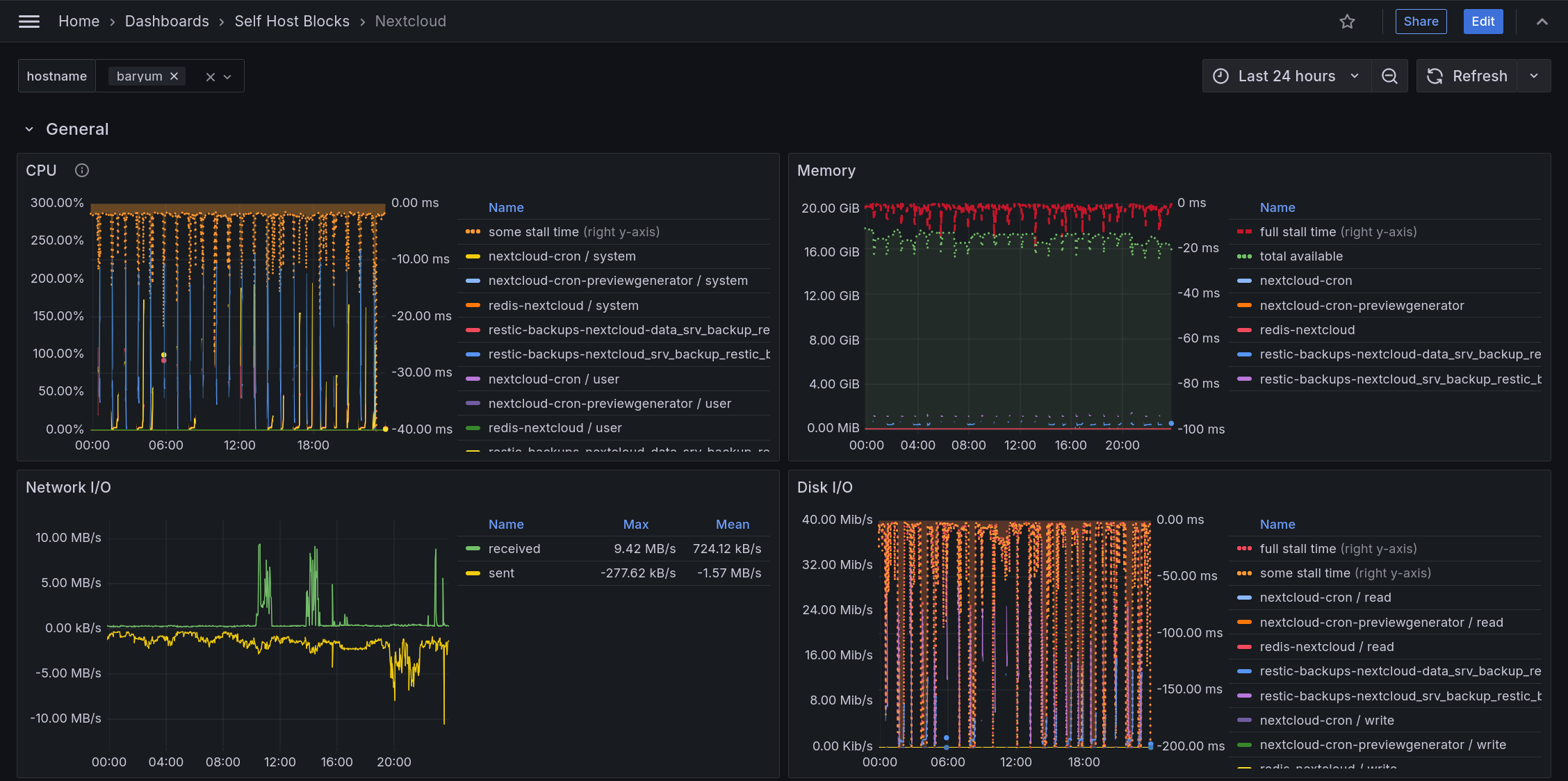
The dashboard is added to Grafana automatically under “Self Host Blocks > Nextcloud” as long as the Nextcloud service is enabled as well as the monitoring block.
The General section shows Nextcloud related services. This includes cronjobs, Redis and backup jobs.
CPU shows stall time which means CPU is maxed out. This graph is inverted so having a small area at the top means the stall time is low.
Memory shows stall time which means some job is waiting on memory to be allocated. This graph is inverted so having a small area at the top means the stall time is low. Some stall time will always be present. Under 10% is fine but having constantly over 50% usually means available memory is low and SWAP is being used. Memory also shows available memory which is the remaining allocatable memory.
Caveat: Network I/O shows the network input and output for all services running, not only those related to Nextcloud.
Disk I/O shows “some” stall time which means some jobs were waiting on disk I/O. Disk is usually the slowest bottleneck so having “some” stall time is not surprising. Fixing this can be done by using disks allowing higher speeds or switching to SSDs. If the “full” stall time is shown, this means all jobs were waiting on disk i/o which can be more worrying. This could indicate a failing disk if “full” stall time appeared recently. These graphs are inverted so having a small area at the top means the stall time is low. Memory also shows available memory which is the remaining allocatable memory.
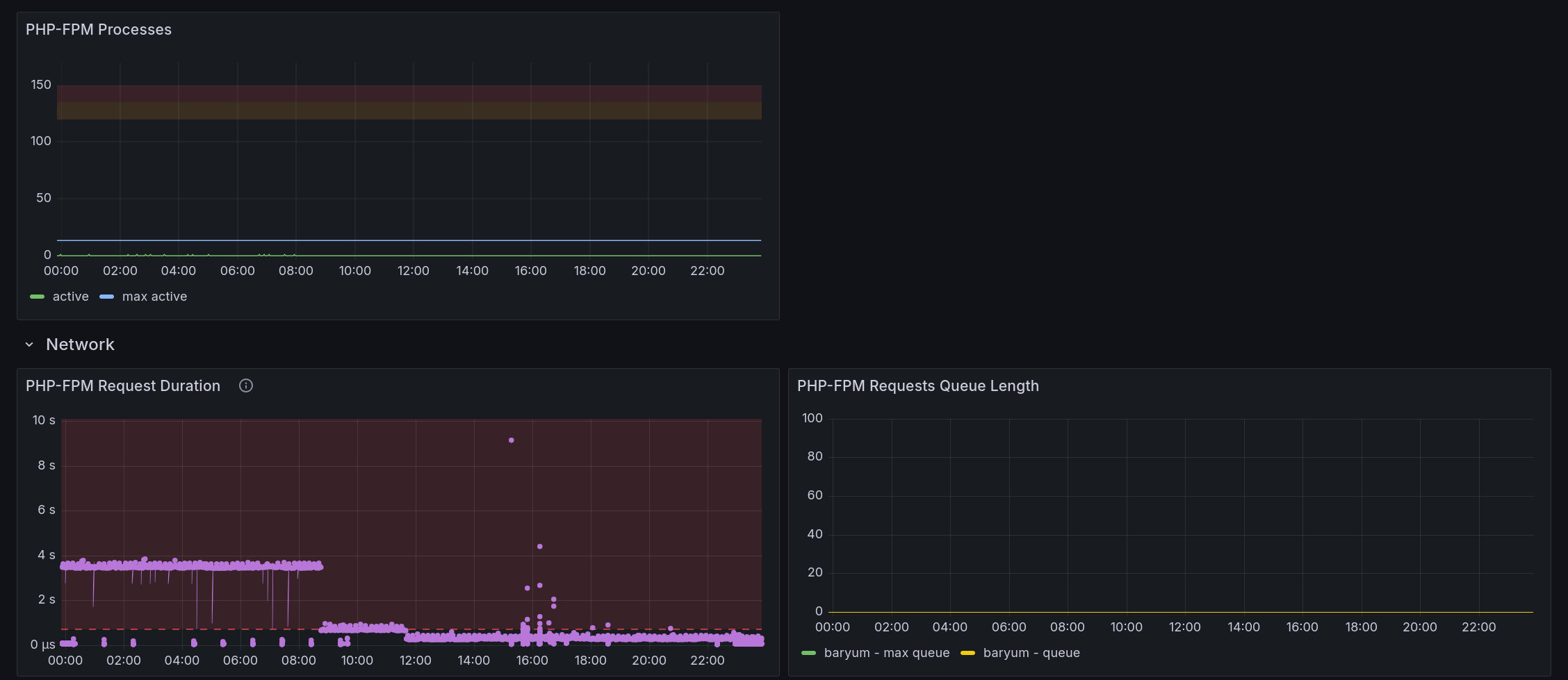
PHP-FPM Processes shows how many processes are used by PHP-FPM. The orange area goes from 80% to 90% of the maximum allowed processes. The read area goes from 90% to 100% of the maximum allowed processes. If the number of active processes reaches those areas once in a while, that’s fine but if it happens most of the time, the maximum allowed processes should be increased.
PHP-FPM Request Duration shows one dot per request and how long it took. Request time is fine if it is under 400ms. If most requests take longer than that, some tracing is required to understand which subsystem is taking some time. That being said, maybe another graph in this dashboard will show why the requests are slow - like disk or other processes hoarding some resources running at the same time.
PHP-FPM Requests Queue Length shows how many requests are waiting to be picked up by a PHP-FPM process. Usually, this graph won’t show anything as long as the PHP-FPM Processes graph is not in the red area. Fixing this requires also increasing the maximum allowed processes.
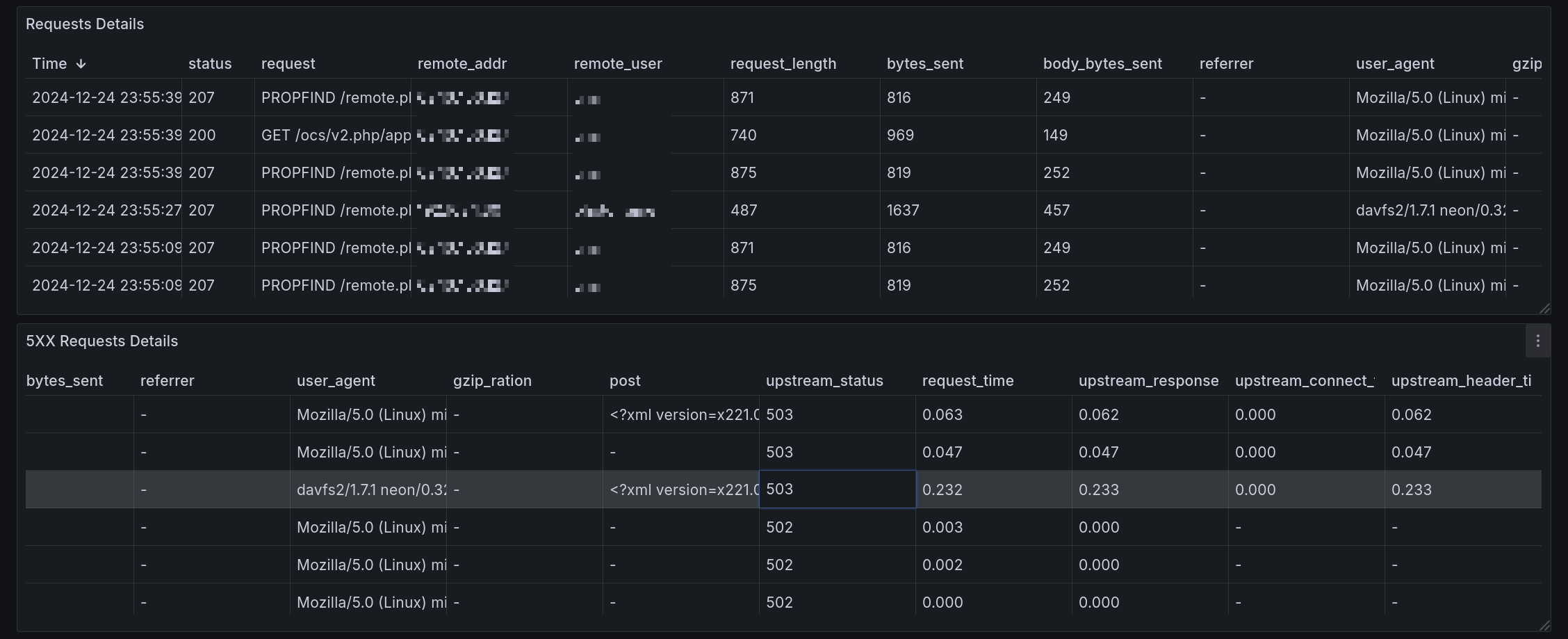
Requests Details shows all requests to the Nextcloud service and the related headers.
5XX Requests Details shows only the requests having a 500 to 599 http status. Having any requests appearing here should be investigated as soon as possible.
Log: <service name> shows all logs from related systemd
<service name>.servicejob. Having no line here most often means the job ran at a time not currently included in the time range of the dashboard.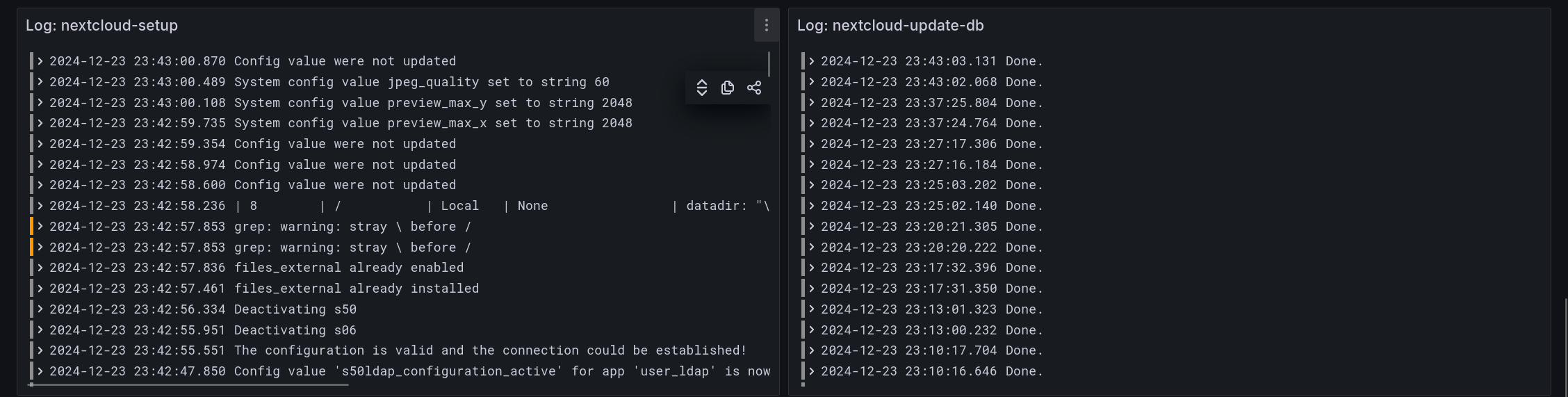
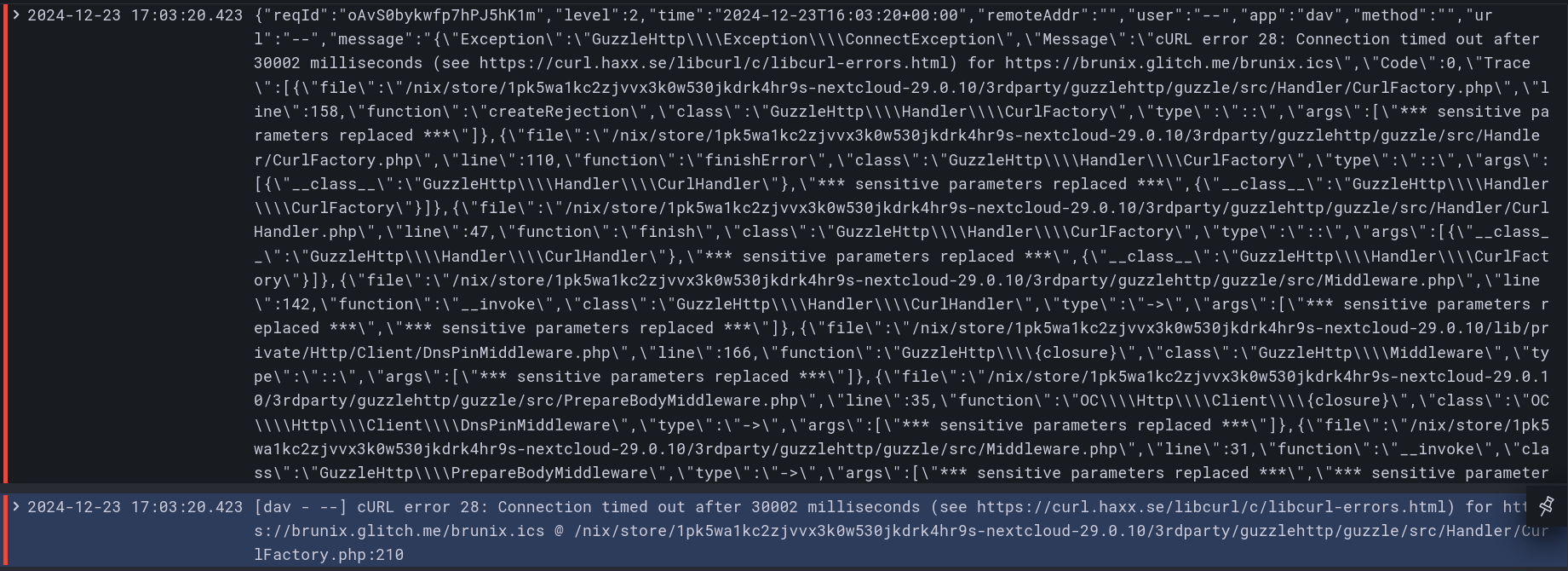
A lot of care has been taken to parse error messages correctly. Nextcloud mixes json and non-json messages so extracting errors from json messages was not that easy. Also, the stacktrace is reduced. The result though is IMO pretty nice as can be seen by the following screenshot. The top line is the original json message and the bottom one is the parsed error.
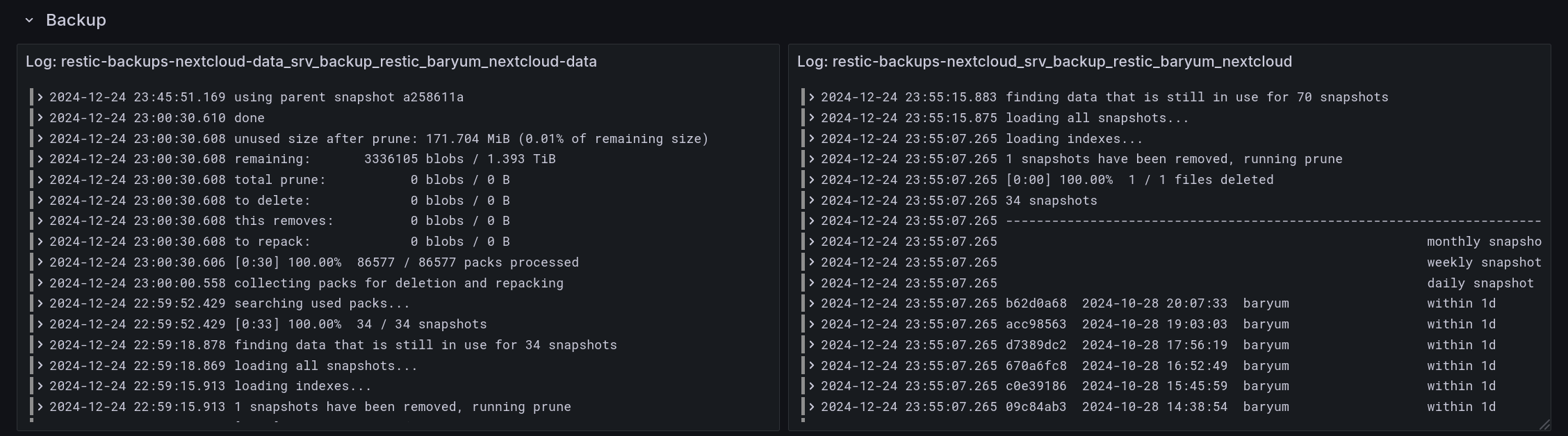
Backup logs show the output of the backup jobs. Here, there are two backup jobs, one for the core files of Nextcloud stored on an SSD which includes the appdata folder. The other backup job is for the external data stored on HDDs which contain all user files.
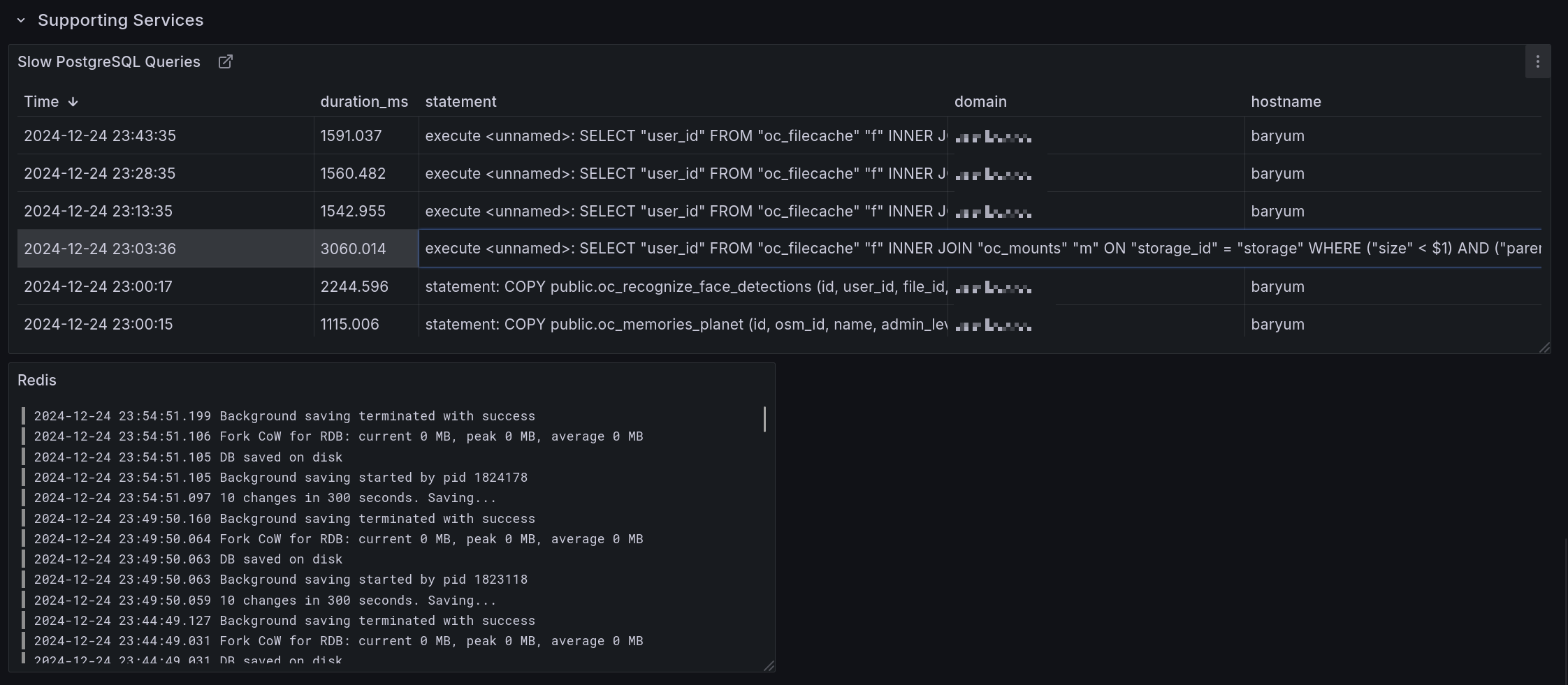
Slow PostgreSQL queries shows all database queries taking longer than 1s to run.
Redis shows all Redis log output.
Debug
On the command line, the occ tool is called nextcloud-occ.
In case of an issue, check the logs for any systemd service mentioned in this section.
On startup, the oneshot systemd service nextcloud-setup.service starts. After it finishes, the
phpfpm-nextcloud.service starts to serve Nextcloud. The nginx.service is used as the reverse
proxy. postgresql.service run the database.
Nextcloud’ configuration is found at ${shb.nextcloud.dataDir}/config/config.php. Nginx’
configuration can be found with systemctl cat nginx | grep -om 1 -e "[^ ]\+conf".
Enable verbose logging by setting the shb.nextcloud.debug boolean to true.
Access the database with sudo -u nextcloud psql.
Access Redis with sudo -u nextcloud redis-cli -s /run/redis-nextcloud/redis.sock.
Options Reference
-
shb.nextcloud.enable -
Whether to enable the SHB Nextcloud service.
Type: boolean
Default:
falseExample:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.enableDashboard -
Whether to enable the Nextcloud SHB dashboard.
Type: boolean
Default:
trueExample:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.adminPass -
Nextcloud admin password.
Type: submodule
Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.adminPass.request -
Request part of the secret contract.
Options set by the requester module enforcing some properties the secret should have.
Type: submodule
Default:
""Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.adminPass.request.group -
Linux group owning the secret file.
Type: string
Default:
"root"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.adminPass.request.mode -
Mode of the secret file.
Type: string
Default:
"0400"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.adminPass.request.owner -
Linux user owning the secret file.
Type: string
Default:
"nextcloud"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.adminPass.request.restartUnits -
Systemd units to restart after the secret is updated.
Type: list of string
Default:
[ "phpfpm-nextcloud.service" ]Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.adminPass.result -
Result part of the secret contract.
Options set by the provider module that indicates where the secret can be found.
Type: submodule
Default:
{ path = "/run/secrets/secret"; }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.adminPass.result.path -
Path to the file containing the secret generated out of band.
This path will exist after deploying to a target host, it is not available through the nix store.
Type: absolute path
Default:
"/run/secrets/secret"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.adminUser -
Username of the initial admin user.
Type: string
Default:
"root"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.alwaysApplyExpensiveMigrations -
Run
occ maintenance:repair --include-expensiveon service start.Larger instances should disable this and run the command at a convenient time but Self Host Blocks assumes that it will not be the case for most users.
Type: boolean
Default:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps -
Applications to enable in Nextcloud. Enabling an application here will also configure various services needed for this application.
Enabled apps will automatically be installed, enabled and configured, so no need to do that through the UI. You can still make changes but they will be overridden on next deploy. You can still install and configure other apps through the UI.
Type: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.externalStorage -
External Storage App. Manual
Set
userLocalMountto automatically add a local directory as an external storage. Use this option if you want to store user data in another folder or another hard drive altogether.In the
directoryoption, you can use either$userand/or$homewhich will be replaced by the user’s name and home directory.Recommended use of this option is to have the Nextcloud’s
dataDiron a SSD and theuserLocalRooDirectoryon a HDD. Indeed, a SSD is much quicker than a spinning hard drive, which is well suited for randomly accessing small files like thumbnails. On the other side, a spinning hard drive can store more data which is well suited for storing user data.Type: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.externalStorage.enable -
Whether to enable Nextcloud External Storage App.
Type: boolean
Default:
falseExample:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.externalStorage.userLocalMount -
If set, adds a local mount as external storage.
Type: null or (submodule)
Default:
nullDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.externalStorage.userLocalMount.directory -
Local directory on the filesystem to mount. Use
$userand/or$homewhich will be replaced by the user’s name and home directory.Type: string
Example:
"/srv/nextcloud/$user"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.externalStorage.userLocalMount.mountName -
Path of the mount in Nextcloud. Use
/to mount as the root.Type: string
Default:
""Example:
[ "home" "/" ]Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap -
LDAP Integration App. Manual
Enabling this app will create a new LDAP configuration or update one that exists with the given host.
Type: null or (submodule)
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.enable -
Whether to enable LDAP app…
Type: boolean
Default:
falseExample:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.adminName -
Admin user of the LDAP server.
Type: string
Default:
"admin"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.adminPassword -
LDAP server admin password.
Type: submodule
Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.adminPassword.request -
Request part of the secret contract.
Options set by the requester module enforcing some properties the secret should have.
Type: submodule
Default:
""Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.adminPassword.request.group -
Linux group owning the secret file.
Type: string
Default:
"root"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.adminPassword.request.mode -
Mode of the secret file.
Type: string
Default:
"0400"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.adminPassword.request.owner -
Linux user owning the secret file.
Type: string
Default:
"nextcloud"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.adminPassword.request.restartUnits -
Systemd units to restart after the secret is updated.
Type: list of string
Default:
[ "phpfpm-nextcloud.service" ]Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.adminPassword.result -
Result part of the secret contract.
Options set by the provider module that indicates where the secret can be found.
Type: submodule
Default:
{ path = "/run/secrets/secret"; }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.adminPassword.result.path -
Path to the file containing the secret generated out of band.
This path will exist after deploying to a target host, it is not available through the nix store.
Type: absolute path
Default:
"/run/secrets/secret"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.configID -
Multiple LDAP configs can co-exist with only one active at a time. This option sets the config ID used by Self Host Blocks.
Type: signed integer
Default:
50Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.dcdomain -
dc domain for ldap.
Type: string
Example:
"dc=mydomain,dc=com"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.host -
Host serving the LDAP server.
Type: string
Default:
"127.0.0.1"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.port -
Port of the service serving the LDAP server.
Type: 16 bit unsigned integer; between 0 and 65535 (both inclusive)
Default:
389Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.ldap.userGroup -
Group users must belong to to be able to login to Nextcloud.
Type: string
Default:
"nextcloud_user"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.memories -
Memories App. Nextcloud App Store
Enabling this app will set up the Memories app and configure all its dependencies.
On first install, you can either let the cron job index all images or you can run it manually with:
nextcloud-occ memories:indexType: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.memories.enable -
Whether to enable Memories app…
Type: boolean
Default:
falseExample:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.memories.photosPath -
Path where photos are stored in Nextcloud.
Type: string
Default:
"/Photos"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.memories.vaapi -
Enable VAAPI transcoding.
Will make
nextclouduser part of therendergroup to be able to access/dev/dri/renderD128.Type: boolean
Default:
falseDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.onlyoffice -
Only Office App. Nextcloud App Store
Enabling this app will also start an OnlyOffice instance accessible at the given subdomain from the given network range.
Type: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.onlyoffice.enable -
Whether to enable Nextcloud OnlyOffice App.
Type: boolean
Default:
falseExample:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.onlyoffice.jwtSecretFile -
File containing the JWT secret. This option is required.
Must be readable by the nextcloud system user.
Type: null or absolute path
Default:
nullDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.onlyoffice.localNetworkIPRange -
Local network range, to restrict access to Open Office to only those IPs.
Type: string
Default:
"192.168.1.1/24"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.onlyoffice.ssl -
Path to SSL files
Type: null or (open submodule of anything)
Default:
nullDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.onlyoffice.ssl.paths -
Paths where the files for the certificate will be located.
This option is the contract output of the
shb.certs.certsSSL block.Type: open submodule of anything
Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.onlyoffice.ssl.paths.cert -
Path to the cert file.
Type: absolute path
Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.onlyoffice.ssl.paths.key -
Path to the key file.
Type: absolute path
Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.onlyoffice.ssl.systemdService -
Systemd oneshot service used to generate the certificate. Ends with the
.servicesuffix.Use this if downstream services must wait for the certificates to be generated before starting.
Type: string
Example:
"cert-generator.service"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.onlyoffice.subdomain -
Subdomain under which Only Office will be served.
Type: string
Default:
"oo"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.previewgenerator -
Preview Generator App. Nextcloud App Store
Enabling this app will create a cron job running every minute to generate thumbnails for new and updated files.
To generate thumbnails for already existing files, run:
nextcloud-occ -vvv preview:generate-allType: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.previewgenerator.enable -
Whether to enable Nextcloud Preview Generator App.
Type: boolean
Default:
falseExample:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.previewgenerator.debug -
Enable more verbose logging.
Type: boolean
Default:
falseExample:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.previewgenerator.recommendedSettings -
Better defaults than the defaults. Taken from this article.
Sets the following options:
nextcloud-occ config:app:set previewgenerator squareSizes --value="32 256" nextcloud-occ config:app:set previewgenerator widthSizes --value="256 384" nextcloud-occ config:app:set previewgenerator heightSizes --value="256" nextcloud-occ config:system:set preview_max_x --type integer --value 2048 nextcloud-occ config:system:set preview_max_y --type integer --value 2048 nextcloud-occ config:system:set jpeg_quality --value 60 nextcloud-occ config:app:set preview jpeg_quality --value=60Type: boolean
Default:
trueExample:
falseDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.recognize -
Recognize App. Nextcloud App Store
Enabling this app will set up the Recognize app and configure all its dependencies.
Type: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.recognize.enable -
Whether to enable Recognize app…
Type: boolean
Default:
falseExample:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso -
SSO Integration App. Manual
Type: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.enable -
Whether to enable SSO app…
Type: boolean
Default:
falseExample:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.adminGroup -
Group admins must belong to to be able to login to Nextcloud.
This option is purposely not inside the LDAP app because only SSO allows distinguising between users and admins.
Type: string
Default:
"nextcloud_admin"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.authorization_policy -
Require one factor (password) or two factor (device) authentication.
Type: one of “one_factor”, “two_factor”
Default:
"one_factor"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.clientID -
Client ID for the OIDC endpoint.
Type: string
Default:
"nextcloud"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.endpoint -
OIDC endpoint for SSO.
Type: string
Example:
"https://authelia.example.com"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.fallbackDefaultAuth -
Fallback to normal Nextcloud auth if something goes wrong with the SSO app. Usually, you want to enable this to transfer existing users to LDAP and then you can disabled it.
Type: boolean
Default:
falseDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.port -
If given, adds a port to the endpoint.
Type: null or 16 bit unsigned integer; between 0 and 65535 (both inclusive)
Default:
nullDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.provider -
OIDC provider name, used for display.
Type: value “Authelia” (singular enum)
Default:
"Authelia"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secret -
OIDC shared secret.
Type: submodule
Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secret.request -
Request part of the secret contract.
Options set by the requester module enforcing some properties the secret should have.
Type: submodule
Default:
""Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secret.request.group -
Linux group owning the secret file.
Type: string
Default:
"root"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secret.request.mode -
Mode of the secret file.
Type: string
Default:
"0400"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secret.request.owner -
Linux user owning the secret file.
Type: string
Default:
"nextcloud"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secret.request.restartUnits -
Systemd units to restart after the secret is updated.
Type: list of string
Default:
[ "phpfpm-nextcloud.service" ]Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secret.result -
Result part of the secret contract.
Options set by the provider module that indicates where the secret can be found.
Type: submodule
Default:
{ path = "/run/secrets/secret"; }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secret.result.path -
Path to the file containing the secret generated out of band.
This path will exist after deploying to a target host, it is not available through the nix store.
Type: absolute path
Default:
"/run/secrets/secret"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secretForAuthelia -
OIDC shared secret. Content must be the same as
secretFileoption.Type: submodule
Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secretForAuthelia.request -
Request part of the secret contract.
Options set by the requester module enforcing some properties the secret should have.
Type: submodule
Default:
""Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secretForAuthelia.request.group -
Linux group owning the secret file.
Type: string
Default:
"root"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secretForAuthelia.request.mode -
Mode of the secret file.
Type: string
Default:
"0400"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secretForAuthelia.request.owner -
Linux user owning the secret file.
Type: string
Default:
"authelia"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secretForAuthelia.request.restartUnits -
Systemd units to restart after the secret is updated.
Type: list of string
Default:
[ ]Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secretForAuthelia.result -
Result part of the secret contract.
Options set by the provider module that indicates where the secret can be found.
Type: submodule
Default:
{ path = "/run/secrets/secret"; }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.apps.sso.secretForAuthelia.result.path -
Path to the file containing the secret generated out of band.
This path will exist after deploying to a target host, it is not available through the nix store.
Type: absolute path
Default:
"/run/secrets/secret"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.autoDisableMaintenanceModeOnStart -
Upon starting the service, disable maintenance mode if set.
This is useful if a deploy failed and you try to redeploy.
Type: boolean
Default:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.backup -
Backup configuration.
Type: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.backup.request -
Request part of the backup contract.
Options set by the requester module enforcing how to backup files.
Type: submodule
Default:
""Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.backup.request.excludePatterns -
File patterns to exclude.
Type: list of string
Default:
[ ".rnd" ]Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.backup.request.hooks -
Hooks to run around the backup.
Type: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.backup.request.hooks.afterBackup -
Hooks to run after backup.
Type: list of string
Default:
[ ]Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.backup.request.hooks.beforeBackup -
Hooks to run before backup.
Type: list of string
Default:
[ ]Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.backup.request.sourceDirectories -
Directories to backup.
Type: non-empty (list of string)
Default:
[ "/var/lib/nextcloud" ]Example:
"/var/lib/vaultwarden"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.backup.request.user -
Unix user doing the backups.
Type: string
Default:
"nextcloud"Example:
"vaultwarden"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.backup.result -
Result part of the backup contract.
Options set by the provider module that indicates the name of the backup and restore scripts.
Type: submodule
Default:
""Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.backup.result.backupService -
Name of service backing up the database.
This script can be ran manually to backup the database:
$ systemctl start backup.serviceType: string
Default:
"backup.service"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.backup.result.restoreScript -
Name of script that can restore the database. One can then list snapshots with:
$ restore snapshotsAnd restore the database with:
$ restore restore latestType: string
Default:
"restore"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.dashboard -
Dashboard contract consumer
Type: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.dashboard.request -
Request part of the dashboard contract.
Type: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.dashboard.request.externalUrl -
URL at which the service can be accessed.
This URL should go through the reverse proxy.
Type: string
Default:
"https://\${config.shb.nextcloud.subdomain}.\${config.shb.nextcloud.domain}"Example:
"https://jellyfin.example.com"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.dashboard.request.internalUrl -
URL at which the service can be accessed directly.
This URL should bypass the reverse proxy. It can be used for example to ping the service and making sure it is up and running correctly.
Type: null or string
Default:
"https://\${config.shb.nextcloud.subdomain}.\${config.shb.nextcloud.domain}"Example:
"http://127.0.0.1:8081"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.dashboard.result -
Result part of the dashboard contract.
No option is provided here.
Type: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.dataDir -
Folder where Nextcloud will store all its data.
Type: string
Default:
"/var/lib/nextcloud"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.debug -
Enable more verbose logging.
Type: boolean
Default:
falseExample:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.defaultPhoneRegion -
Two letters region defining default region.
Type: string
Example:
"US"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.domain -
Domain under which Nextcloud is served.
<subdomain>.<domain>[:<port>]Type: string
Example:
"domain.com"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.externalFqdn -
External fqdn used to access Nextcloud. Defaults to <subdomain>.<domain>. This should only be set if you include the port when accessing Nextcloud.
Type: null or string
Default:
nullExample:
"nextcloud.domain.com:8080"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.extraApps -
Extra apps to install.
Should be a function returning an
attrSetofappidas keys topackagesas values, like generated byfetchNextcloudApp. The appid must be identical to theidvalue in the apps’appinfo/info.xml. Search in nixpkgs for theNN.jsonfiles for existing apps.You can still install apps through the appstore.
Type: raw value
Default:
nullExample:
apps: { inherit (apps) mail calendar contact; phonetrack = pkgs.fetchNextcloudApp { name = "phonetrack"; sha256 = "0qf366vbahyl27p9mshfma1as4nvql6w75zy2zk5xwwbp343vsbc"; url = "https://gitlab.com/eneiluj/phonetrack-oc/-/wikis/uploads/931aaaf8dca24bf31a7e169a83c17235/phonetrack-0.6.9.tar.gz"; version = "0.6.9"; }; }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.maxUploadSize -
The upload limit for files. This changes the relevant options in php.ini and nginx if enabled.
Type: string
Default:
"4G"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.mountPointServices -
If given, all the systemd services and timers will depend on the specified mount point systemd services.
Type: list of string
Default:
[ ]Example:
["var.mount"]Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.phpFpmPoolSettings -
Settings for PHPFPM.
Type: null or (attribute set of anything)
Default:
{ pm = "static"; "pm.max_children" = 5; "pm.start_servers" = 5; }Example:
{ "pm" = "dynamic"; "pm.max_children" = 50; "pm.start_servers" = 25; "pm.min_spare_servers" = 10; "pm.max_spare_servers" = 20; "pm.max_spawn_rate" = 50; "pm.max_requests" = 50; "pm.process_idle_timeout" = "20s"; }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.phpFpmPrometheusExporter -
Settings for exporting
Type: submodule
Default:
{ }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.phpFpmPrometheusExporter.enable -
Enable export of php-fpm metrics to Prometheus.
Type: boolean
Default:
trueDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.phpFpmPrometheusExporter.port -
Port on which the exporter will listen.
Type: 16 bit unsigned integer; between 0 and 65535 (both inclusive)
Default:
8300Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.port -
Port under which Nextcloud will be served. If null is given, then the port is omitted.
<subdomain>.<domain>[:<port>]Type: null or 16 bit unsigned integer; between 0 and 65535 (both inclusive)
Default:
nullDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.postgresSettings -
Settings for the PostgreSQL database.
Go to https://pgtune.leopard.in.ua/ and copy the generated configuration here.
Type: null or (attribute set of string)
Default:
nullExample:
{ # From https://pgtune.leopard.in.ua/ with: # DB Version: 14 # OS Type: linux # DB Type: dw # Total Memory (RAM): 7 GB # CPUs num: 4 # Connections num: 100 # Data Storage: ssd max_connections = "100"; shared_buffers = "1792MB"; effective_cache_size = "5376MB"; maintenance_work_mem = "896MB"; checkpoint_completion_target = "0.9"; wal_buffers = "16MB"; default_statistics_target = "500"; random_page_cost = "1.1"; effective_io_concurrency = "200"; work_mem = "4587kB"; huge_pages = "off"; min_wal_size = "4GB"; max_wal_size = "16GB"; max_worker_processes = "4"; max_parallel_workers_per_gather = "2"; max_parallel_workers = "4"; max_parallel_maintenance_workers = "2"; }Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.ssl -
Path to SSL files
Type: null or (open submodule of anything)
Default:
nullDeclared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.ssl.paths -
Paths where the files for the certificate will be located.
This option is the contract output of the
shb.certs.certsSSL block.Type: open submodule of anything
Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.ssl.paths.cert -
Path to the cert file.
Type: absolute path
Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.ssl.paths.key -
Path to the key file.
Type: absolute path
Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.ssl.systemdService -
Systemd oneshot service used to generate the certificate. Ends with the
.servicesuffix.Use this if downstream services must wait for the certificates to be generated before starting.
Type: string
Example:
"cert-generator.service"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.subdomain -
Subdomain under which Nextcloud will be served.
<subdomain>.<domain>[:<port>]Type: string
Example:
"nextcloud"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.tracing -
Enable xdebug tracing.
To trigger writing a trace to
/var/log/xdebug, add a the following header:XDEBUG_TRACE <shb.nextcloud.tracing value>The response will contain the following header:
x-xdebug-profile-filename /var/log/xdebug/cachegrind.out.63484Type: null or string
Default:
nullExample:
"debug_me"Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix> -
shb.nextcloud.version -
Nextcloud version to choose from.
Type: one of 31, 32
Default:
31Declared by:
<selfhostblocks/modules/services/nextcloud-server.nix>